Roles and Permissions
Overview
Roles control user and group access to administrative functions within Universal Controller. A user or group that has been assigned a role has permission to perform any function defined for that role.
Permissions control user and group access to specific functions for specific types of Controller records.
Some roles have permissions for specific functions that can be assigned individually. For example, a user that has been assigned the ops_agent_cluster_admin role has permission to perform all functions associated with Agent Clusters. A user that has not been assigned the ops_agent_cluster_admin role still can be given permission to perform individual functions associated with Agent Clusters via the Agent Cluster Permissions.
Conversely, since there is no role associated with Agents, permissions for a user to perform functions associated with Agents must be assigned specific Agent Permissions.
Note
The ops_admin role assigns a user permission to perform all functions.
Assigning Roles to Users or Groups
Roles control user access to functions that include:
- Setting up security.
- Creating reports, filters, and gauges.
- Creating Agent Clusters, SNMP Managers.
- Creating Email Connections, Database Connections, PeopleSoft Connections, and SAP Connections.
- Creating and promoting bundles of records.
Each role is a predefined collection of administrative functions (see Description of Roles, below). By assigning a role to a user or group, you automatically give that user or group all functions associated with that role.
Note
You cannot add new roles to the Controller; you must assign administrative functions to groups or users using the predefined roles.
To assign roles to a user or group:
Step 1 | |
|---|---|
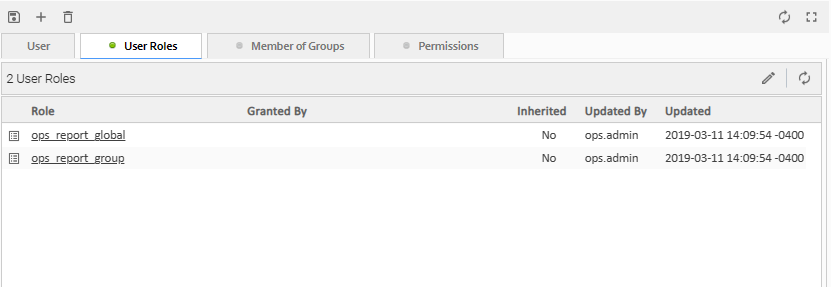
Step 2 | For a User, click the User Roles tab. A list of Roles assigned to the User displays. |
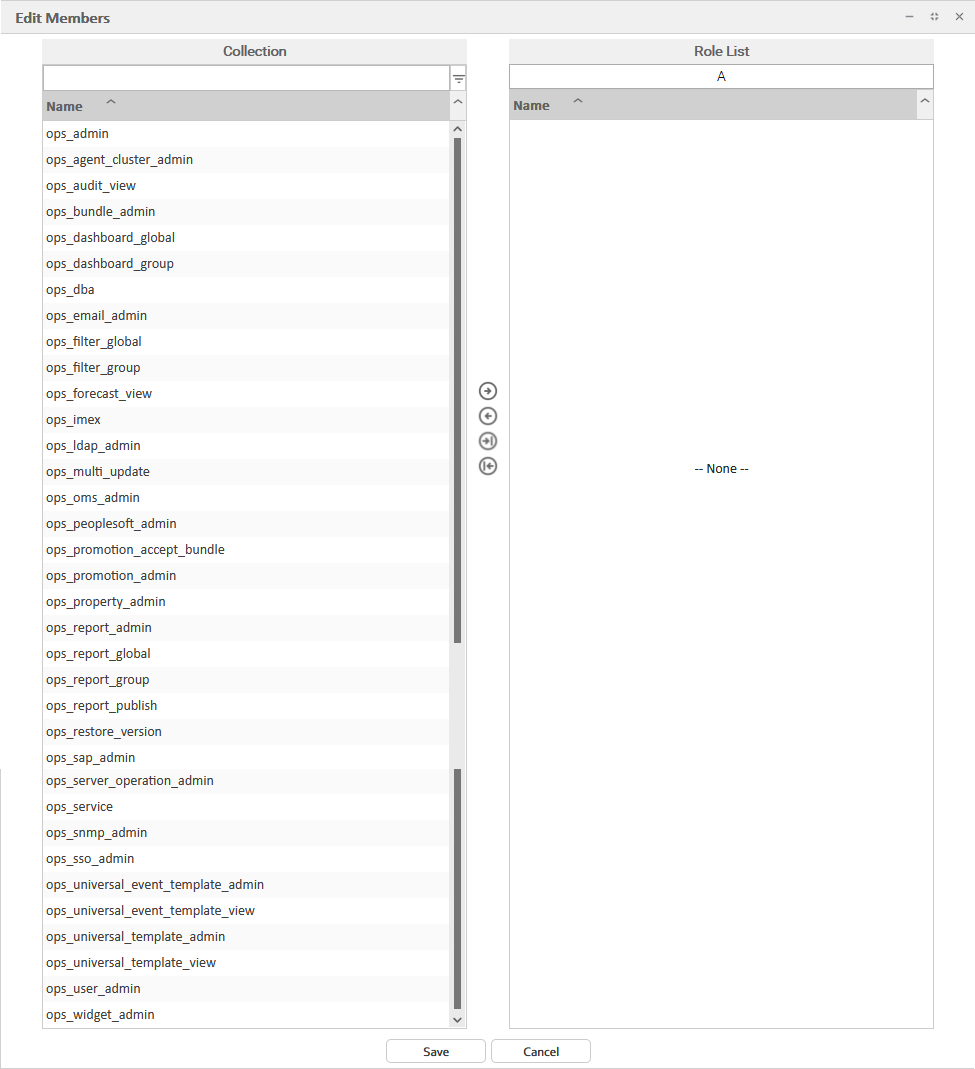
Step 3 | Click Edit. An Edit Members pop-up displays that allows you to assign Roles to the User / Group. For example:
|
Step 4 | To filter the Users/Groups listed in the Collection window, enter characters in the text field above the Name column. Only Users/Groups containing that sequence of characters will display in the list. |
Step 5 | To assign a Role to the User / Group, move the Role from the Collection window to the Roles window:
To unassign a Role to the User / Group, move the Role from the Roles window to the Collection window:
|
Step 6 | Click Save. |
Description of Roles
The following table summarizes the roles available in the Controller.
Role Name | Available Functions | Contains Roles |
|---|---|---|
ops_admin | All functions; this is the Universal Controller administrator role. The easiest way to assign full permissions to a user is to add the user to the Administrator Group, which by default is assigned the ops_admin role. Note The ops_admin role contains all other roles. If a user is assigned the ops_admin role, no other roles need to be assigned to that user, and unassigning any other role from the user will not revoke that role. |
|
ops_agent_cluster_admin | Create, read, update, and delete agent clusters. | |
ops_audit_view | Read all Audits. If Audit Owner Read Permitted system property = true, users can view their own audits without having either the ops_admin role or the ops_audit_view role. | |
ops_bundle_admin |
(Also see Bundle Permissions and Promotion Target Permissions, below.) | |
ops_dashboard_global | Create, update, and delete Dashboard Details with Everyone visibility; updating includes updating Dashboard visibility. | |
ops_dashboard_group | Create, update, and delete Dashboard Details that are visible for a group in which this user is a member; updating includes updating Dashboard visibility. | |
ops_dba | Create, update, delete Database Connections. | |
ops_email_admin | Create, read, update, delete Email Connections. | |
ops_filter_global | Create Filters with Everyone visibility. | |
ops_filter_group | Create Filters that belong to a group of which this user is a member. | |
ops_forecast_view | Read Forecast Calendar, Forecasts List, and Forecast Details. Note Users also can read forecast information, without being assigned this role, if they have Read permission for the Task specified in the Forecast Details. | |
ops_imex | List Import/Export XML. | |
ops_ldap_admin | Read and update LDAP Settings. | |
ops_multi_update | ||
| ops_oauth_admin | Create, read, update, and delete OAuth Clients. | |
ops_oms_admin | Create, update, and delete OMS Servers. | |
ops_peoplesoft_admin | Create, read, update, and delete PeopleSoft Connections. | |
ops_promotion_accept_bundle | Accept bundles being promoted to a target server. (The Accept Bundle command is executed on the target server automatically as part of the Promote and Promote Bundle commands and does not involve user interaction.) | |
ops_promotion_admin |
Note By default, the ops_promotion_admin role also grants Read permission for any type of definition that can be added to a Bundle, given the expectation that a promotion administrator would review the content of a Bundle before promoting it. To change this default behaviour, see the Promotion Read Permission Required Universal Controller property. |
|
ops_property_admin | Read, update, and delete Universal Controller system properties and Password Settings. | |
ops_report_admin |
The Strict Report Create Constraints Universal Controller system property specifies whether or not to restrict report creation only to users with the ops_admin, ops_report_admin, ops_report_group, or ops_report_global role. |
|
ops_report_global | Create global reports. | |
ops_report_group | Create reports that belong to a group to which this user is a member. | |
ops_report_publish | Publish reports. (This role was applicable only to the Controller 5.x release.) | |
ops_restore_version | Restore old versions of records. | |
ops_sap_admin | Create, read, update, and delete SAP Connections. | |
ops_server_operation_admin | Run Server Operations. | |
ops_service |
| |
| ops_simulation_view | Read Simulation records. | |
ops_snmp_admin | Create, read, update, and delete SNMP Managers, to which the Controller sends SNMP notifications. | |
ops_sso_admin | Read and update Single Sign-On Settings. | |
ops_universal_event_template_admin | Create, read, update, and delete Universal Event Templates. |
|
ops_universal_event_template_view | Read Universal Event Templates. | |
ops_universal_template_admin | Create, read, update, and delete Universal Templates (including Universal Template Event Templates). |
|
ops_universal_template_view | Read Universal Templates (including Universal Template Event Templates). | |
ops_user_admin | Create, read, update, and delete users and groups. |
|
| ops_user_impersonate | Allows an authenticated user to impersonate another user by using the X-Impersonate-User HTTP header on a Web Service request. | |
| ops_webhook_admin |
| |
| ops_webhook_view | Read Webhooks. | |
ops_widget_admin | Create, update, and delete Widgets. |
Assigning Permissions to Users or Groups
Permissions control user access to specific types of Controller records, such as task or trigger, and the types of functions that can be performed for those record types, such as create or delete.
You can further narrow down which records each permission applies to by specifying either name parameters or Business Services. For example, a given permission might apply only to tasks whose name begins with "SF," or a permission might apply only to tasks that have been assigned to a specific Business Service or to tasks that do not belong to any Business Services. See General Permissions Field Descriptions, below, for more details.
To add permissions to a user or group:
Step 1 | |
|---|---|
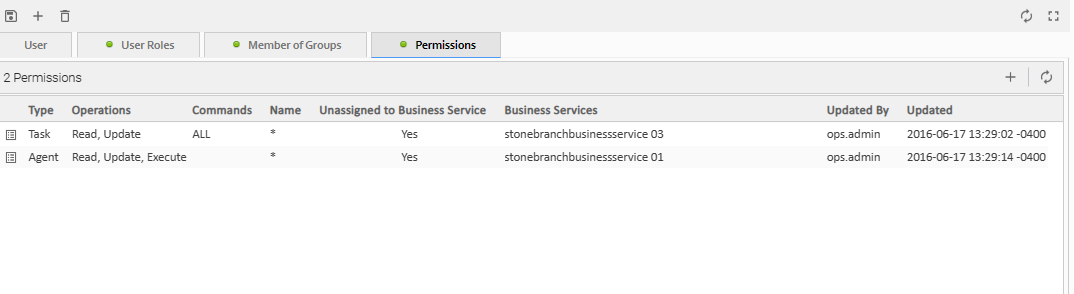
Step 2 | Click the Permissions tab. A list of permissions assigned to the User / Group displays. Note The Business Services column represents a virtual field whose value is determined by data from both the Member of Business Services field and the Member of Any Business Service or Unassigned field. If you want to apply a sort relating to the data in Business Services, you have to add either or both Member of Business Services and Member of Any Business Service or Unassigned fields as columns and apply the desired sort on either or both of them. |
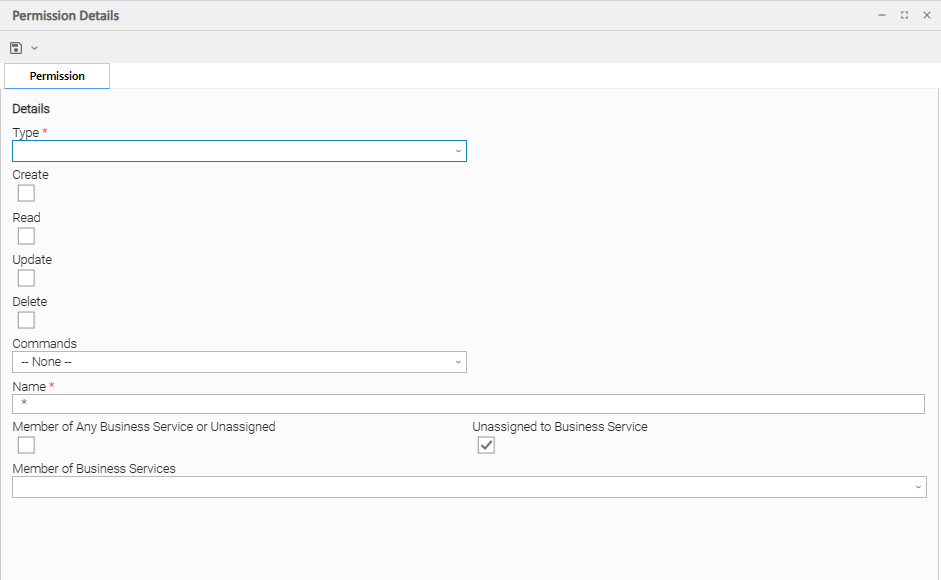
Step 3 | Click New. The Permissions Details pop-up displays. |
Step 4 | Select permissions for the selected user or group.
|
General Permissions Field Descriptions
The following fields of information and buttons display in the Permissions Details for all Permission types:
Field Name | Description |
|---|---|
Details | This section contains detailed information about the permission. |
Name | Applies this permission to records whose name matches the string specified here. Wildcards are supported. |
Member of Any Business Service or Unassigned | Applies this permission both to records that belong to any Business Service and to records that do not belong to any Business Service. |
Unassigned to Business Service | Applies this permission to records that do not belong to any Business Service. If this option is enabled, the user / user group will have the defined permissions on all records that do not belong to any Business Service. |
Member of Business Services | Applies this permission to records that are members of the selected Business Service(s). Click the lock icon to unlock the field and select Business Services. |
Metadata | This section contains Metadata information about this record. |
UUID | Universally Unique Identifier of this record. |
Updated By | Name of the user that last updated this record. |
Updated | Date and time that this record was last updated. |
Created By | Name of the user that created this record. |
Created | Date and time that this record was created. |
Buttons | This section identifies the buttons displayed above and below the Permissions Details that let you perform various actions. |
Save | Saves a new record in the Controller database. |
Save & New | Saves a new record in the Controller database and redisplays empty Details so that you can create another new record. |
Update |
Saves updates to the record. |
Delete |
Deletes the current record. |
Refresh | Refreshes any dynamic data displayed in the Details. |
Close | For pop-up view only; closes the pop-up view of this record. |
Types of Permissions
This section identifies the different types of permissions that you can add to a user or group.
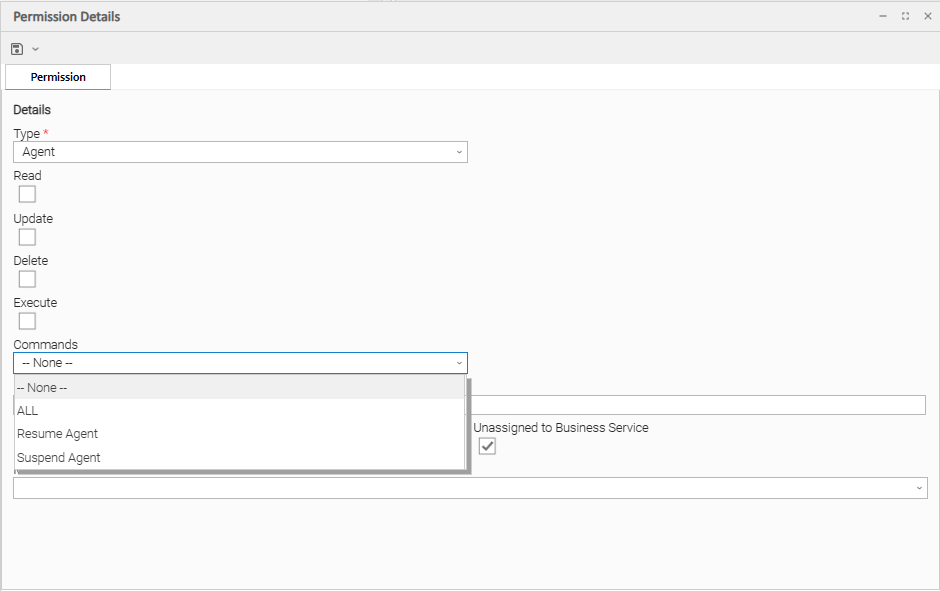
Agent Permissions
Options | Description |
|---|---|
Read | Grants permission to read an Agent definition. The Read check box will be checked automatically if the Business Service Visibility Restricted Universal Controller system property is false. |
Update | Grants permission to update an Agent definition. (Only certain fields can be updated.) |
Delete | Grants permission to delete an Agent. |
Execute | Grants permission to execute a task on an Agent. |
Commands |
|
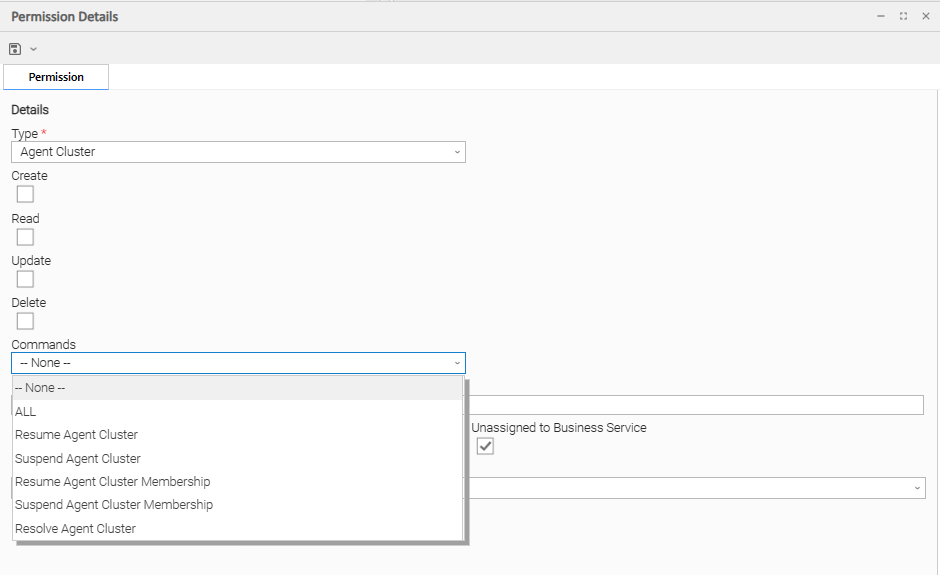
Agent Cluster Permissions
(You also can assign Agent Cluster Permissions to a user by assigning the ops_agent_cluster_admin role to the user.)
Options | Description |
|---|---|
Create | Grants permission to create a new Agent Cluster. |
Read | Grants permission to read an Agent Cluster definition. The Read check box will be checked automatically if the Business Service Visibility Restricted Universal Controller system property is false. |
Update | Grants permission to update an Agent Cluster definition. (Only certain fields can be updated.) |
Delete | Grants permission to delete an Agent Cluster. |
Commands |
|
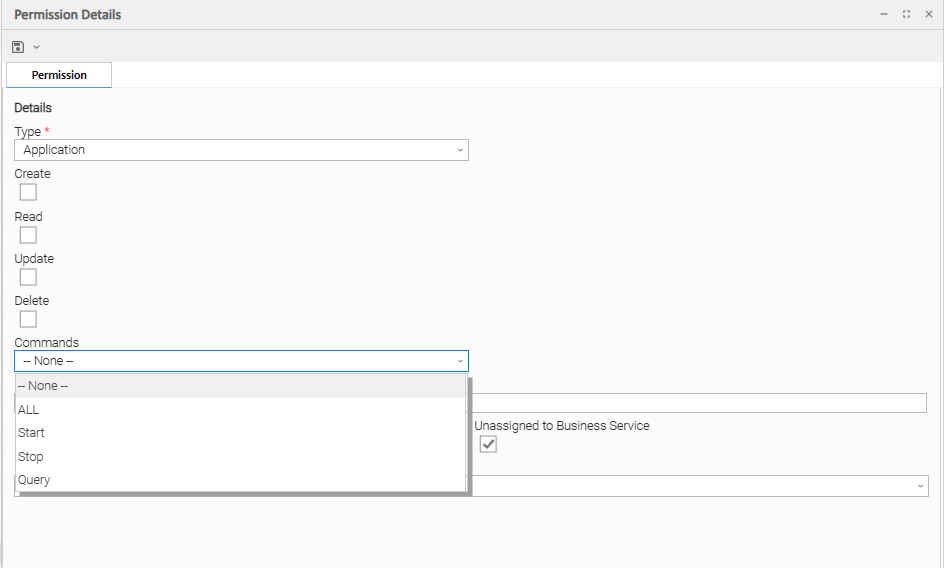
Application Permissions
Options | Description |
|---|---|
Create | Grants permission to create a new Application. |
Read | Grants permission to read an Application. |
Update | Grants permission to update an Application. |
Delete | Grants permission to delete an Application. |
Commands | See Application Control Tasks for details. Options:
|
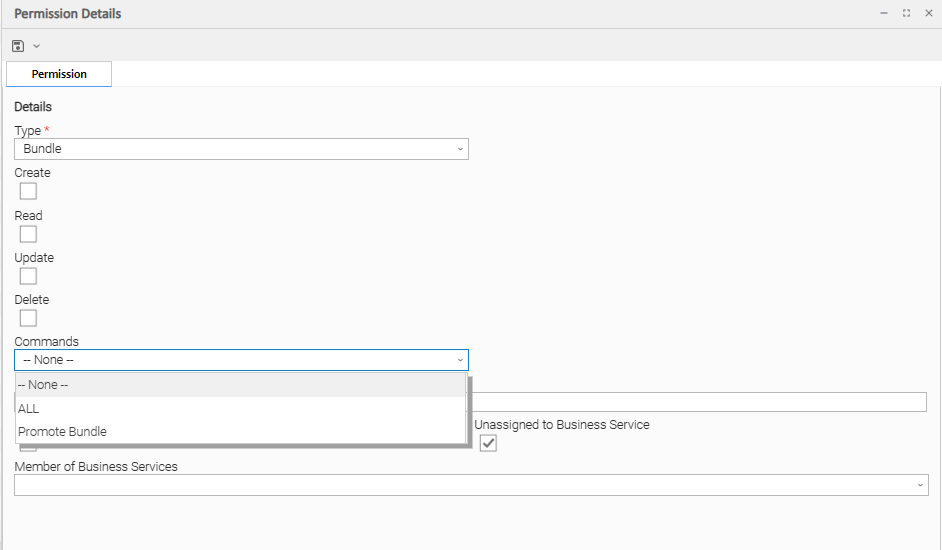
Bundle Permissions
(You also can assign Bundle Permissions to a user by assigning the ops_bundle_admin role to the user.)
Options | Description |
|---|---|
Create | Grants permission to create a Bundle matching both the specified name wildcard and business service membership, including the use of the Create Bundle By Date and Create Bundle By Business Service commands. |
Read | Grants permission to read a Bundle matching both the specified name wildcard and business service membership.
|
Update | Grants permission to update a Bundle matching both the specified name wildcard and business service membership, including the use of the Add To Bundle command. |
Delete | Grants permission to delete a Bundle matching both the specified name wildcard and business service membership. |
Commands |
For the ALL or Promote Bundle command:
|
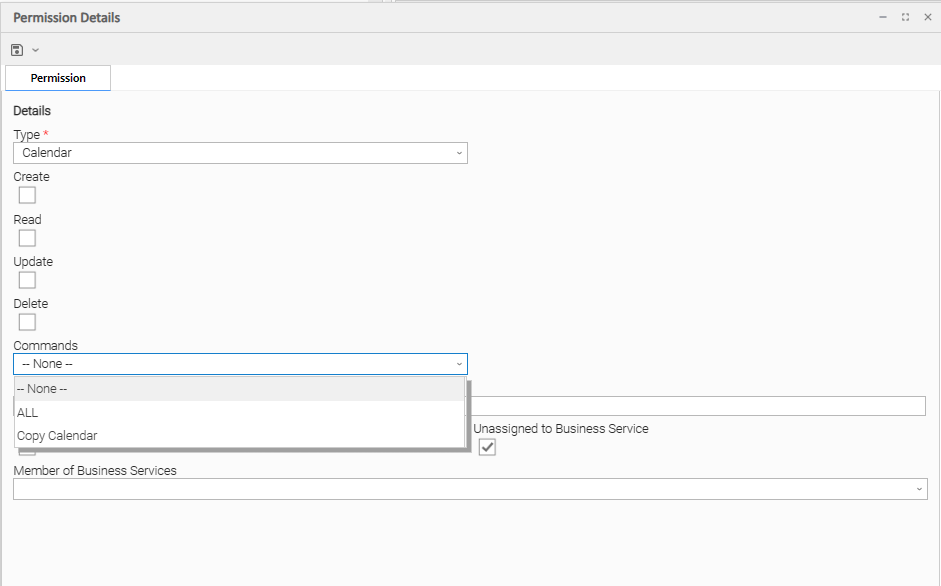
Calendar Permissions
Options | Description |
|---|---|
Create | Grants permission to create a new Calendar. |
Read | Grants permission to read a Calendar. |
Update | Grants permission to update a Calendar. |
Delete | Grants permission to delete a Calendar. |
Commands |
|
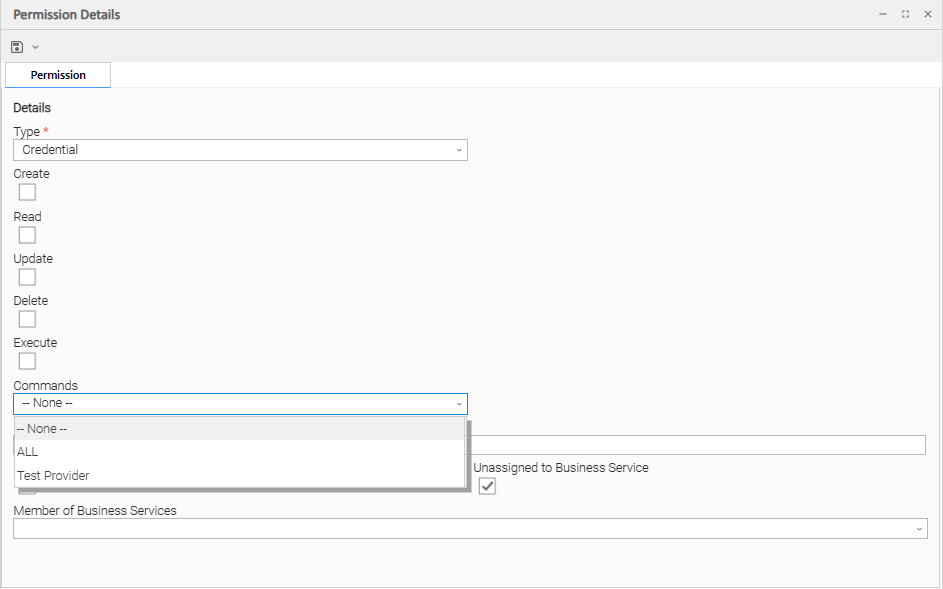
Credential Permissions
Options | Description |
|---|---|
Create | Grants permission to create a new Credential. |
Read | Grants permission to read a Credential. |
Update | Grants permission to update a Credential. |
Delete | Grants permission to delete a Credential. |
Execute | Grants permission to execute a task that requires a Credential. |
Commands | N/A |
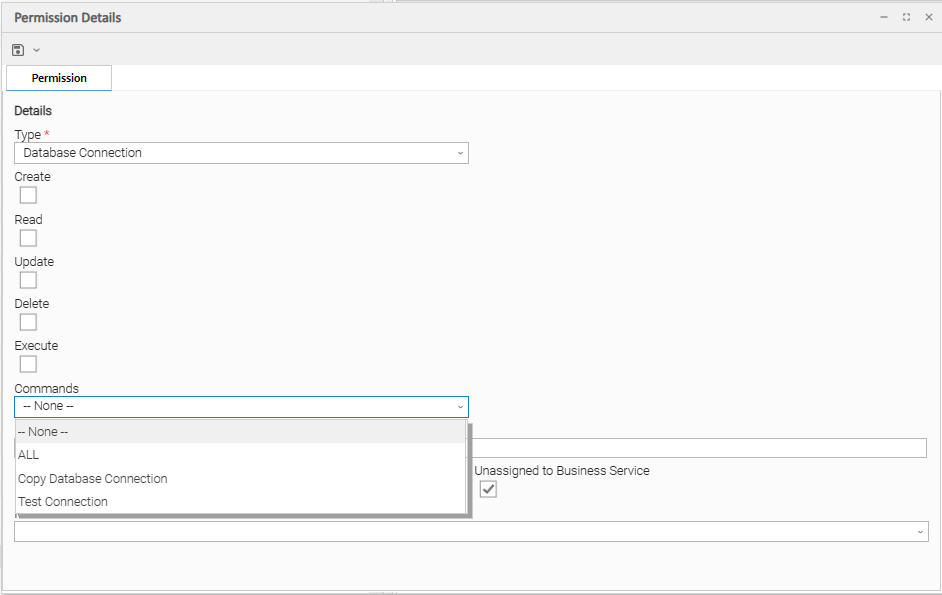
Database Connection Permissions
(You also can assign Database Connection Permissions to a user by assigning the ops_dba role to the user.)
Options | Description |
|---|---|
Create | Grants permission to create a new Database Connection. |
Read | Grants permission to read a Database Connection. |
Update | Grants permission to update a Database Connection. |
Delete | Grants permission to delete a Database Connection. |
Execute | Grants permission to execute a task that requires a Database Connection. (Displays only if the Strict Connection Execute Constraints Universal Controller system property is true.) |
Commands |
|
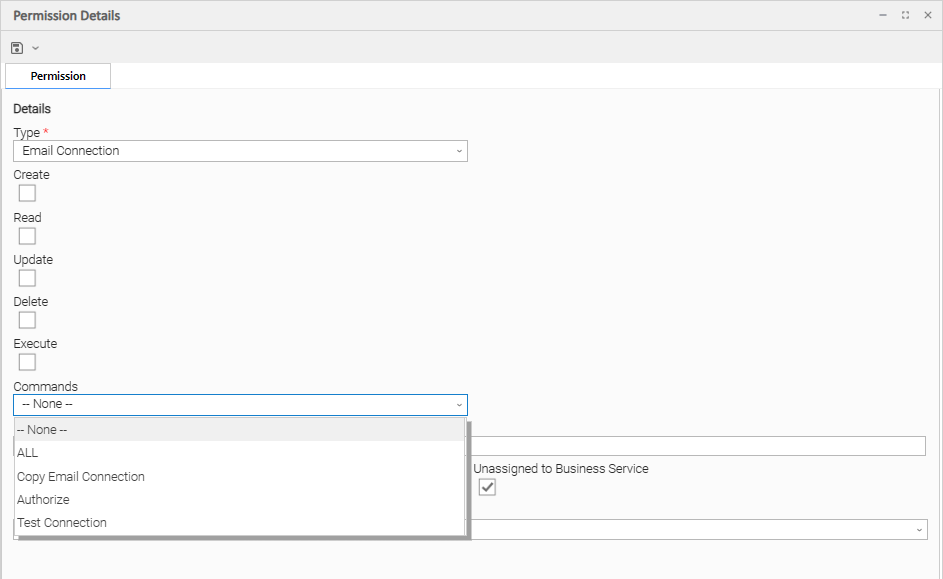
Email Connection Permissions
(You also can assign Email Connection Permissions to a user by assigning the ops_email_admin role to the user.)
Options | Description |
|---|---|
Create | Grants permission to create a new Email Connection. |
Read | Grants permission to read an Email Connection. |
Update | Grants permission to update an Email Connection. |
Delete | Grants permission to delete an Email Connection. |
Execute | Grants permission to execute a task that requires an Email Connection. (Displays only if the Strict Connection Execute Constraints Universal Controller system property is true.) |
Commands |
|
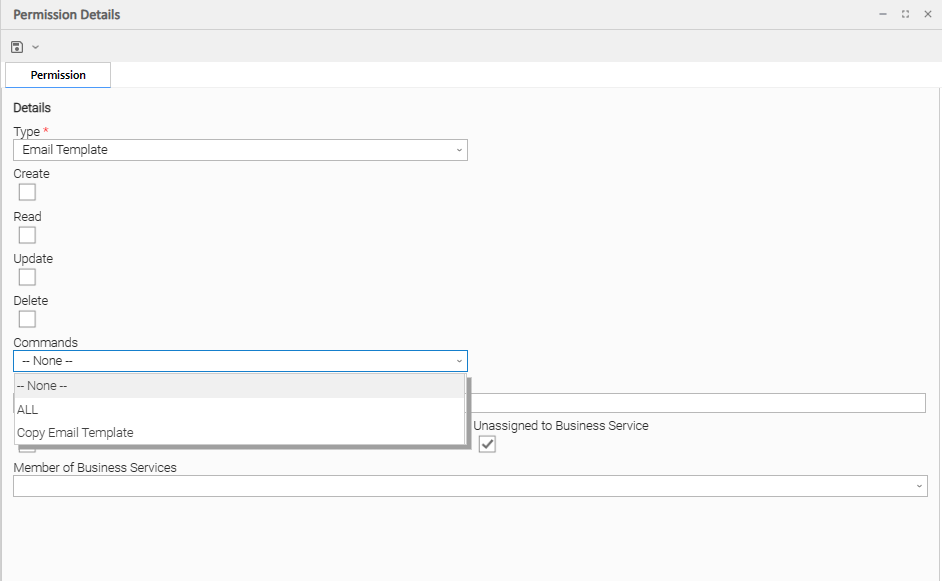
Email Template Permissions
Options | Description |
|---|---|
Create | Grants permission to create a new Email Template. |
Read | Grants permission to read an Email Template. |
Update | Grants permission to update an Email Template. |
Delete | Grants permission to delete an Email Template. |
Commands |
|
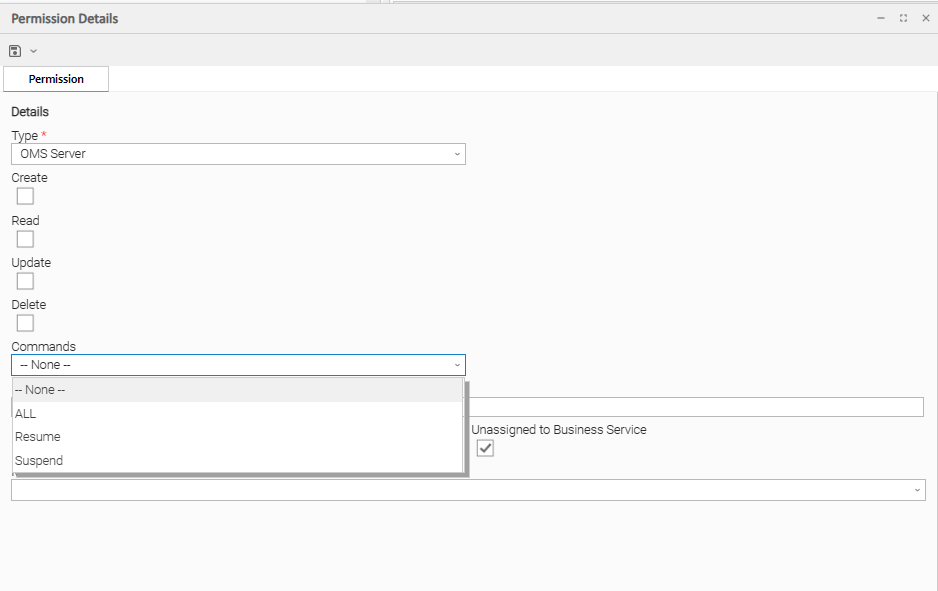
OMS Server Permissions
(You also can assign OMS Server Permissions to a user by assigning the ops_oms_admin role to the user.)
Options | Description |
|---|---|
Create | Grants permission to create a new OMS Server. |
Read | Grants permission to read an OMS Server. |
Update | Grants permission to update an OMS Server. |
Delete | Grants permission to delete an OMS Server. |
Commands |
|
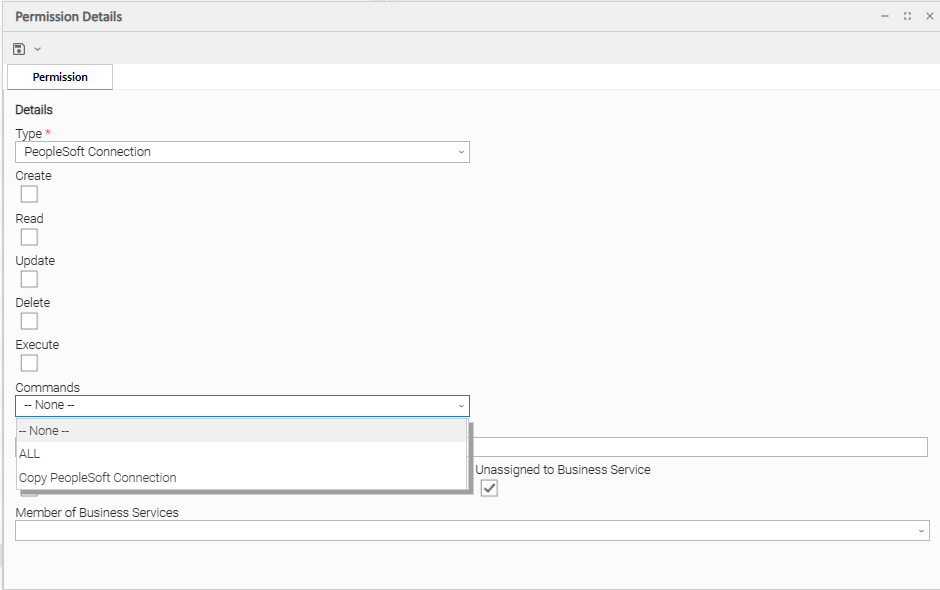
PeopleSoft Connection Permissions
(You also can assign PeopleSoft Connection Permissions to a user by assigning the ops_peoplesoft_admin role to the user.)
Options | Description |
|---|---|
Create | Grants permission to create a new PeopleSoft Connection. |
Read | Grants permission to read a PeopleSoft Connection. |
Update | Grants permission to update a PeopleSoft Connection. |
Delete | Grants permission to delete a PeopleSoft Connection. |
Execute | Grants permission to execute a task that requires a PeopleSoft Connection. (Displays only if the Strict Connection Execute Constraints Universal Controller system property is true.) |
Commands |
|
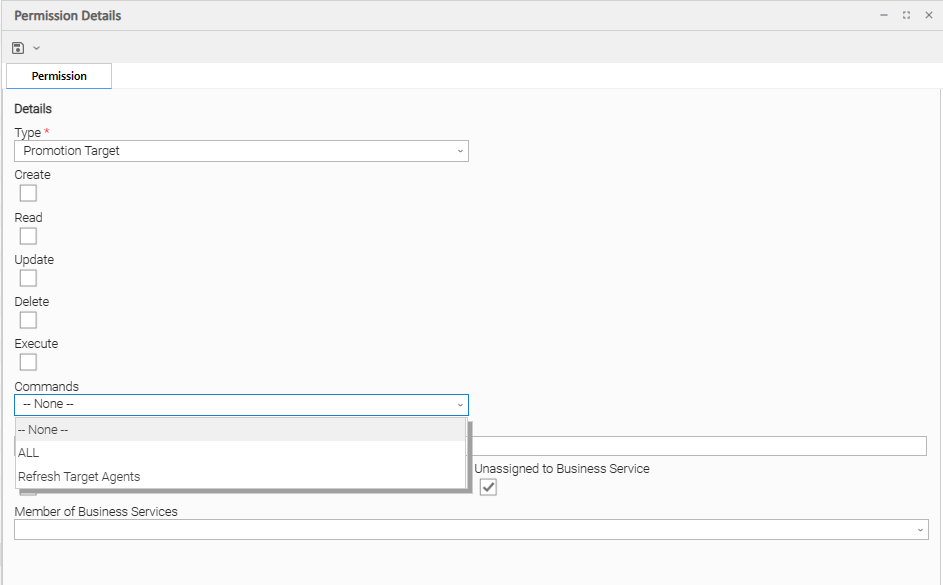
Promotion Target Permissions
(You also can assign Promotion Target Permissions to a user by assigning the ops_promotion_admin role to the user.)
Options | Description |
|---|---|
Create | Grants permission to create a Promotion Target matching both the specified name wildcard and business service membership. |
Read | Grants permission to read a Promotion Target matching both the specified name wildcard and business service membership. |
Update | Grants permission to update a Promotion Target matching both the specified name wildcard and business service membership. |
Delete | Grants permission to delete a Promotion Target matching both the specified name wildcard and business service membership |
Execute | Grants permission to promote a Bundle using a Promotion Target matching both the specified name wildcard and business service membership, assuming the user has both Read permission and Promote Bundle command permission for the Bundle. |
Commands |
|
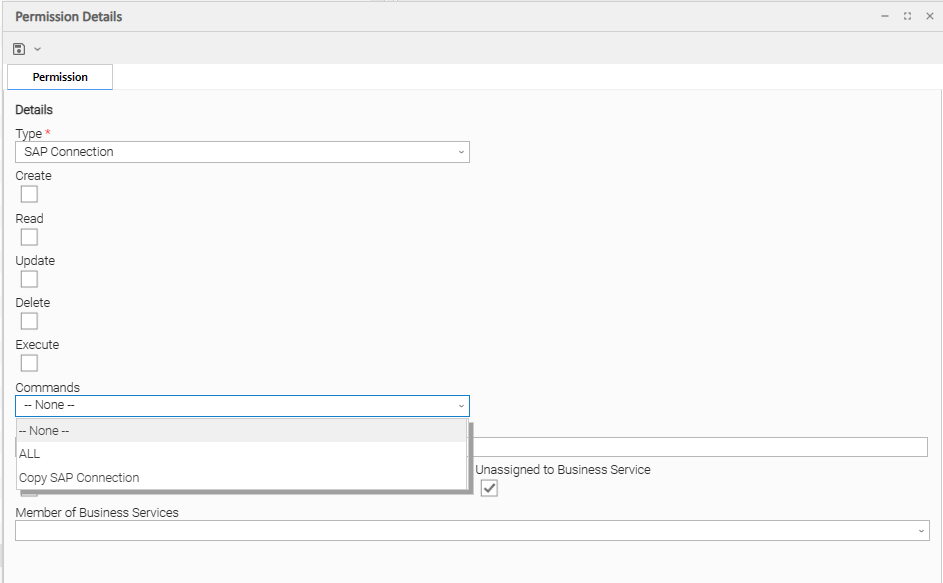
SAP Connection Permissions
(You also can assign SAP Connection Permissions to a user by assigning the ops_sap_admin role to the user.)
Options | Description |
|---|---|
Create | Grants permission to create a new SAP Connection. |
Read | Grants permission to read an SAP Connection. |
Update | Grants permission to update an SAP Connection. |
Delete | Grants permission to delete an SAP Connection. |
Execute | Grants permission to execute a task that requires an SAP Connection. (Displays only if the Strict Connection Execute Constraints Universal Controller system property is true.) |
Commands |
|
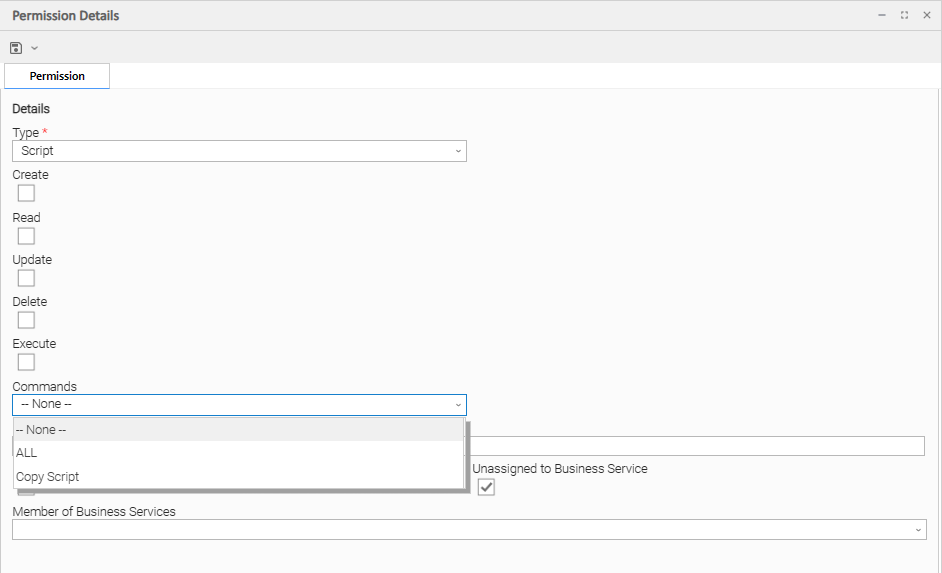
Script Permissions
Options | Description |
|---|---|
Create | Grants permission to create a new Script. |
Read | Grants permission to read a Script. |
Update | Grants permission to update a Script. |
Delete | Grants permission to delete a Script. |
Execute | Grants permission to execute a Script contained by a task. |
Commands |
|
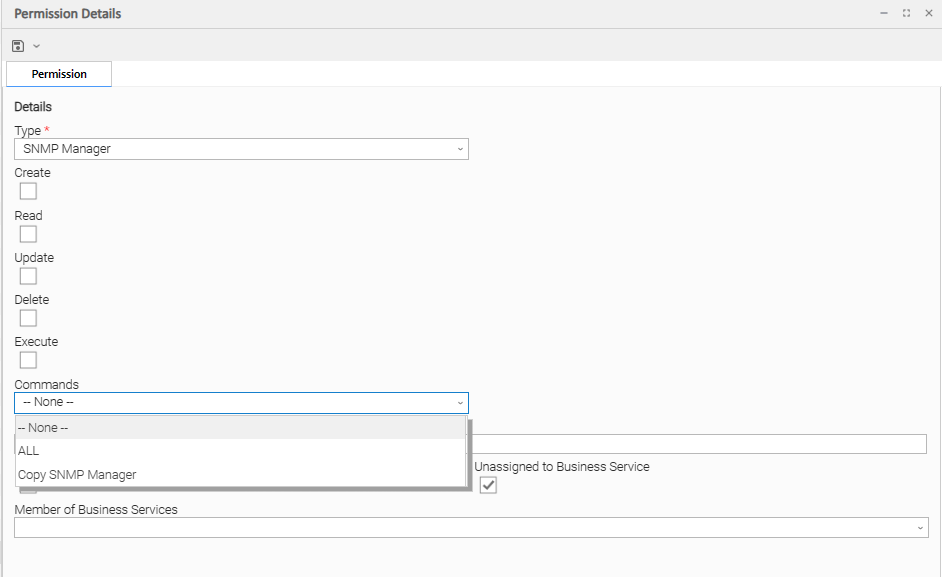
SNMP Manager Permissions
(You also can assign SNMP Manager Permissions to a user by assigning the ops_snmp_admin role to the user.)
Options | Description |
|---|---|
Create | Grants permission to create a new SNMP Manager. |
Read | Grants permission to read an SNMP Manager. |
Update | Grants permission to update an SNMP Manager. |
Delete | Grants permission to delete an SNMP Manager. |
Execute | Grants permission to execute a task that requires an SNMP Manager. (Displays only if the Strict Connection Execute Constraints Universal Controller system property is true.) |
Commands |
|
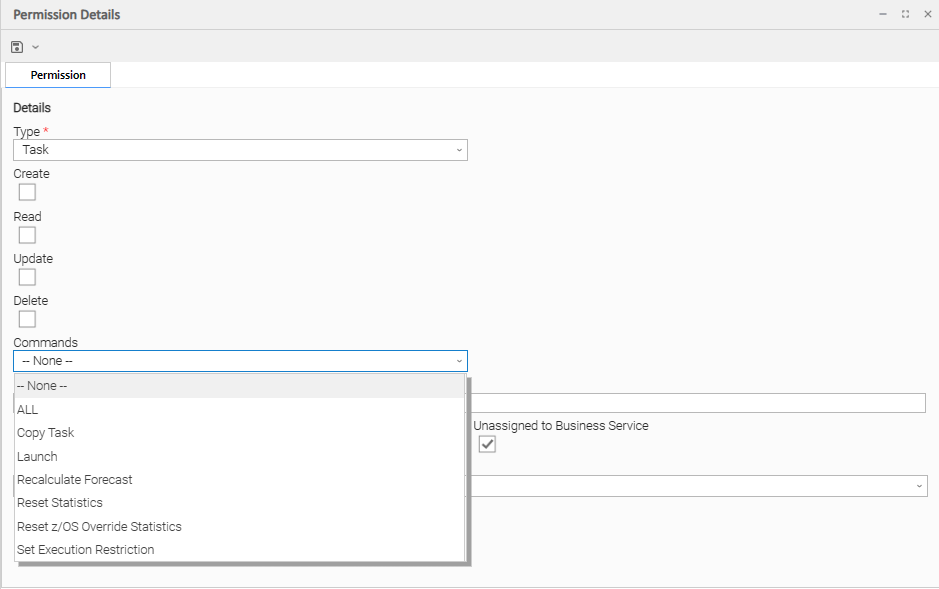
Task Permissions
Options | Description |
|---|---|
Create | Grants permission to create a new Task. |
Read | Grants permission to read a Task. |
Update | Grants permission to update a Task. |
Delete | Grants permission to delete a Task. |
Commands |
|
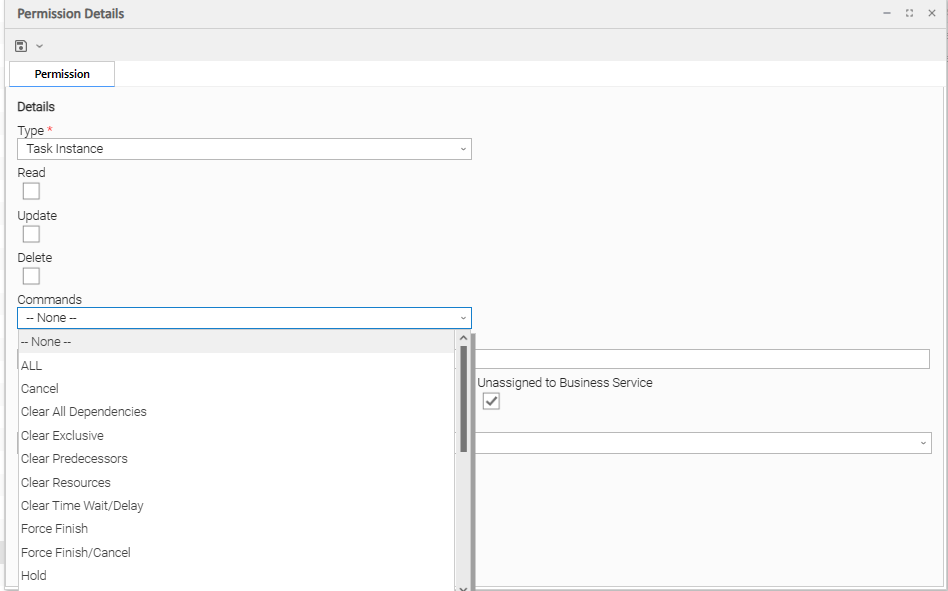
Task Instance Permissions
Options | Description |
|---|---|
Create | Task instances are created automatically when the task launches, so the Create permission does not appear. |
Read | Grants permission to read a Task Instance |
Update | Grants permission to update certain fields on a Task Instance. |
Delete | Grants permission to delete a Task Instance. |
Commands | For command descriptions, see Manually Running and Controlling Tasks.
Note Universal Controller will initially check for command permission specifically for the task instance. If no command permission is granted for the task instance, Universal Controller will check if command permission is granted for the parent workflow task instance, and then continue to check for command permission up the workflow task instance hierarchy. |
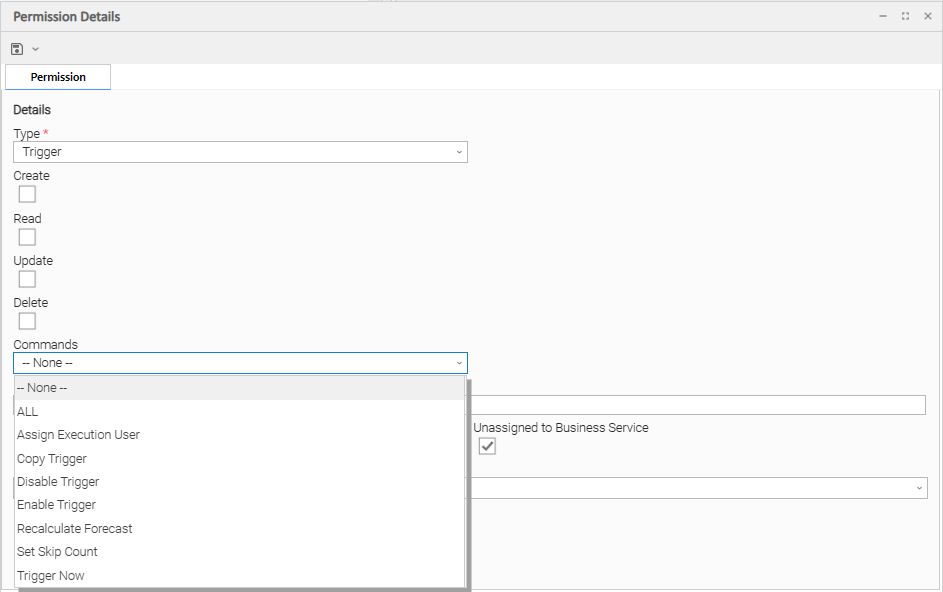
Trigger Permissions
Options | Description |
|---|---|
Create | Grants permission to create a Trigger. |
Read | Grants permission to read a Trigger. |
Update | Grants permission to update a Trigger. |
Delete | Grants permission to delete a Trigger. |
Commands |
|
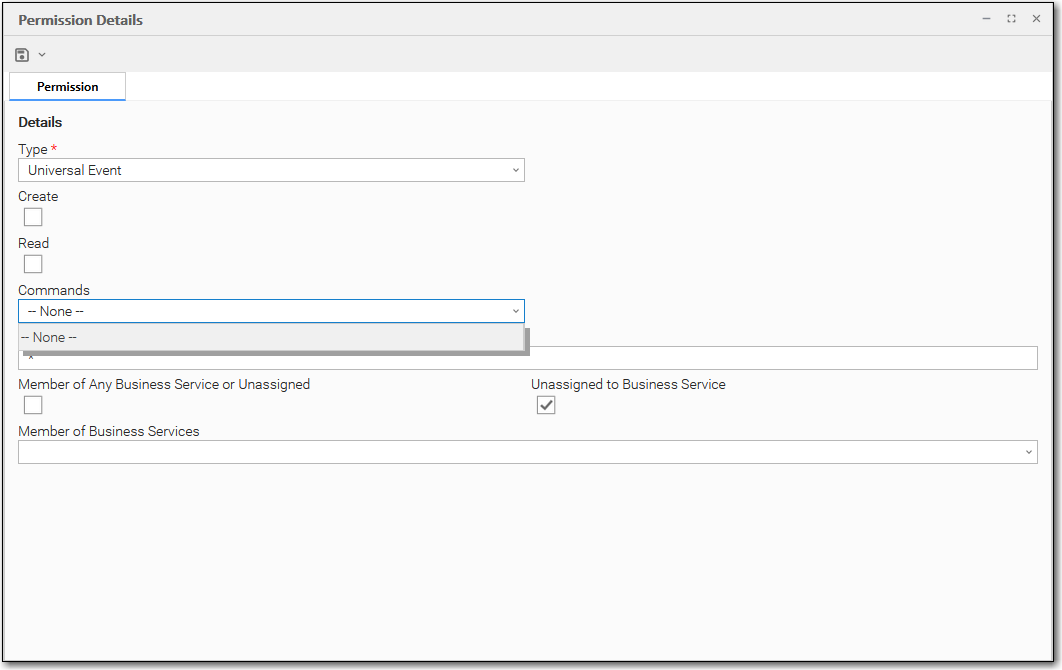
Universal Event Permissions
The authorization for publishing and monitoring Universal Events is separate from the Universal Event Template administration and requires the Universal Event permission.
The permission Name wildcard applies to the published Universal Event Name.
The Name of a published global Universal Event is derived from the Universal Event Template Name.
The Name of a published local Universal Event is derived from the Universal Template Name and the Universal Template Event Template Name.
<template-name>.<event-template-name>
The permission Member of Any Business Service or Unassigned, Unassigned to Business Service, and Member of Business Services applies to the published Universal Event Member of Business Services.
For a global Universal Event published through the Web Service API, the publisher optionally specifies the Member of Business Services.
For a local Universal Event published by a Universal Task Instance Extension, the Universal Event inherits the Universal Task Instance Member of Business Services.
Options | Description |
|---|---|
Create | Grants permission to publish or push Universal Events. |
Read | Grants permission to monitor Universal Events. |
Commands | -- None -- |
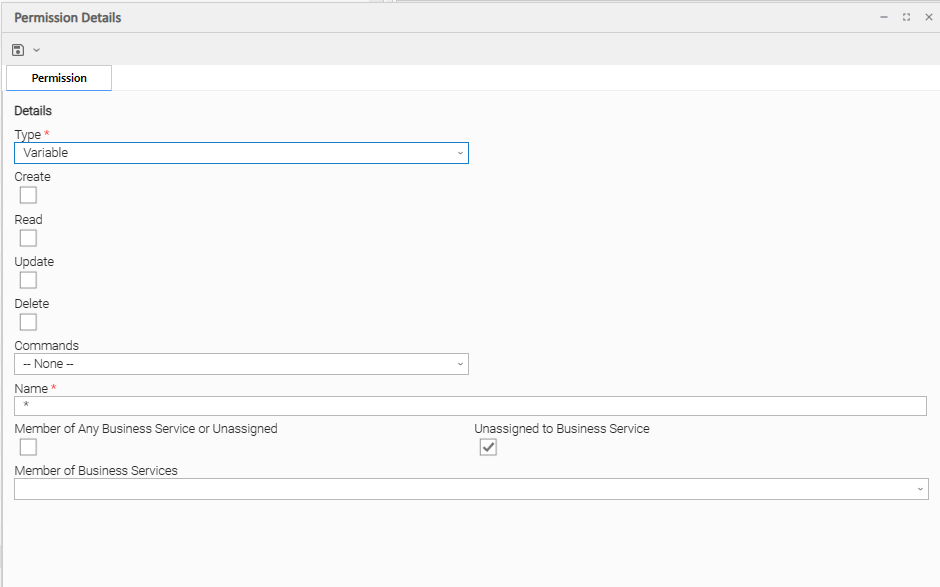
Variable Permissions
Options | Description |
|---|---|
Create | Grants permission to create a Variable. |
Read | Grants permission to read a Variable. |
Update | Grants permission to update a Variable. |
Delete | Grants permission to delete a Variable. |
Commands | N/A |
Enabling / Disabling Enhanced Variable Security
Important
If you have upgraded from a Controller release that did not previously support the Variable permission type, it is important that you review and assign global variable permissions to all appropriate users/groups to avoid impacting existing workload that requires the use of global variables to execute.
By default, enhanced global variable security is enabled; the Variable Security Enabled Universal Controller system property is set to true.
This controls global variable access the following ways:
- Users with the ops_admin role have full access to all global variables.
- Users with the ops_promotion_admin role have Read access to all global variables.
- Create, Read, Update, and Delete permissions must be assigned to users explicitly if those permissions are not granted through the ops_admin or ops_promotion_admin role.
- Only those global variables for which a user has Read permission will be visible from the Variables list.
- Only those global variables for which the Execution User of a task instance has Read permission will be available within the variable scope of a task instance.
- A Set Variable action for a global variable will require appropriate global variable Create or Update permission.
- CLI and Web Services APIs will require appropriate global variable permissions depending on whether the command will Read, Create, or Update a global variable.
- Create Bundle By Date command will only add a global variable to the bundle if the:
- Global variable qualifies for the specified date.
- User invoking the command has Read permission for that global variable.
All defined Variable permissions will be enforced unless enhanced global variable security has been disabled by setting Variable Security Enabled to false. This allows all global variables to be managed and used by any valid Universal Controller user.
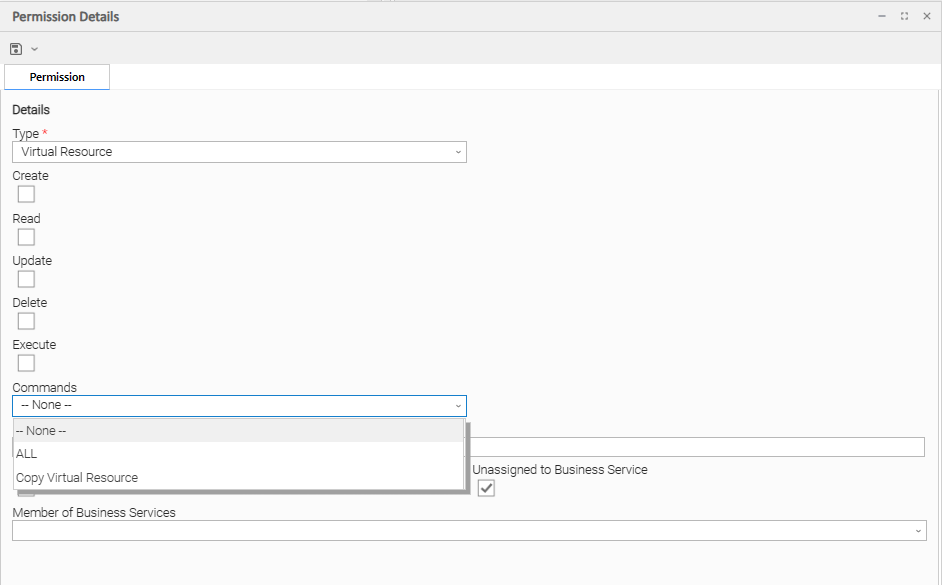
Virtual Resource Permissions
Options | Description |
|---|---|
Create | Grants permission to create a virtual resource. |
Read | Grants permission to read a virtual resource. |
Update | Grants permission to update a virtual resource. |
Delete | Grants permission to delete a virtual resource. |
Execute | Grants permission to execute a virtual resource. |
Commands |
|
Enabling Enhanced Virtual Resource Security
Important
If you have upgraded from a Controller release that did not previously support the Virtual Resource permission type, it is important that you review and assign virtual resource permissions to all appropriate users/groups to avoid impacting existing workload that requires the use of virtual resources to execute.
By default, enhanced virtual resource security is enabled; the Virtual Resource Security Enabled Universal Controller system property is set to true.
This controls virtual resource access the following ways:
- All users will have Read access to virtual resources.
- Users with the ops_admin role will have full access to all virtual resources.
- Create, Update, Delete, and Execution permissions must be explicitly assigned to users if those permissions are not granted through the ops_promotion_admin role.
- Only those virtual resources for which the Execution User of the task instance has Execute permission can be requested by the task instance. Any virtual resource requested by task instances with an Execution User that does not have Execute permission for that virtual resource will result in the task instance going into Start Failure status, with status description Execution for virtual resource "resource-name" prohibited due to security constraints.
- Set Virtual Resource Limit System Operation action will require appropriate virtual resource Update permission.
- CLI and Web Services APIs will require appropriate virtual resource permissions: Updating a virtual resource limit through the CLI and Web Services APIs will require virtual resource Update permission.
All defined Virtual Resource permissions will be enforced unless enhanced virtual resource security has been disabled by setting Virtual Resource Security Enabled to false. This allows all virtual resources to be managed and used by any valid Universal Controller user.
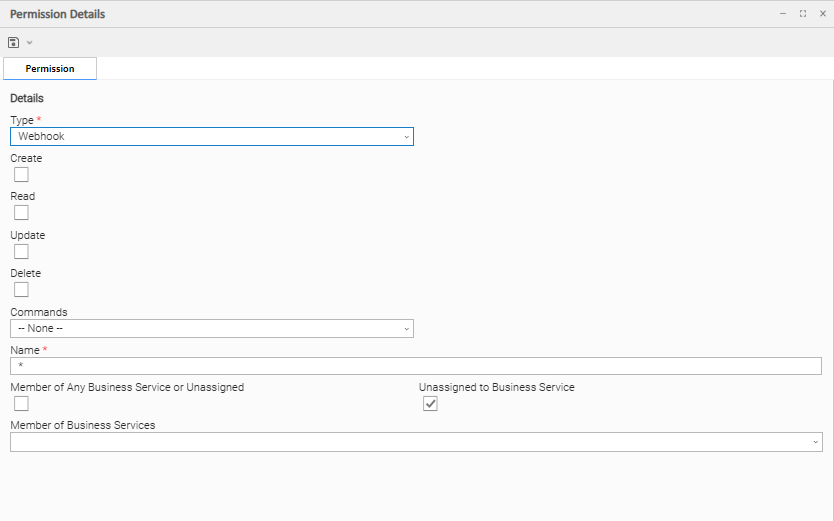
Webhook Permissions
Options | Description |
|---|---|
| Create | Grants permission to create a Webhook. |
| Read | Grants permission to read a Webhook. |
| Update | Grants permission to update a Webhook. |
| Delete | Grants permission to delete a Webhook. |
| Commands |
|
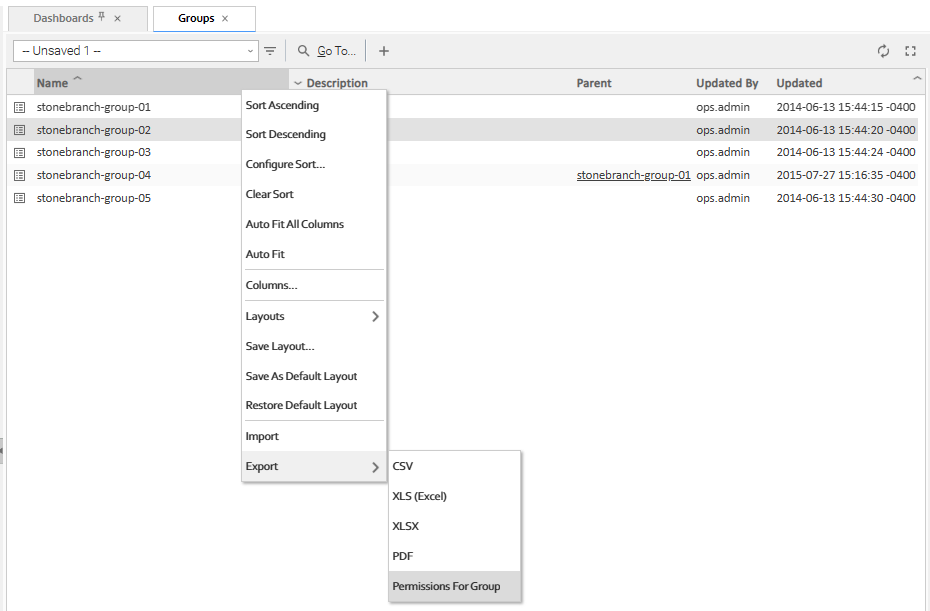
Exporting Permissions for a Group
The Controller lets you export user groups and their permissions, which then can be imported into another Controller system. Only the permissions listed under the Permissions tab for each group will be exported.
Step 1 | From the Administration navigation pane, select Security > Groups. The Groups list displays. |
|---|---|
Step 2 | As desired, filter the list to select the group(s) whose permissions you want to export. When you perform the export, all groups matching the filter will be exported. |
Step 3 | Access the Action menu and select Export > Permissions For Group. |
To export or import the Permissions For Group XML, you must have the ops_admin role or the ops_imex and ops_user_admin roles.
If the groups do not exist on the import system, they (and their Permissions) will be created there.
If the groups do exist on the import system, only the description of the groups and the permissions under their Permissions tab will be replaced with those from the imported XML.